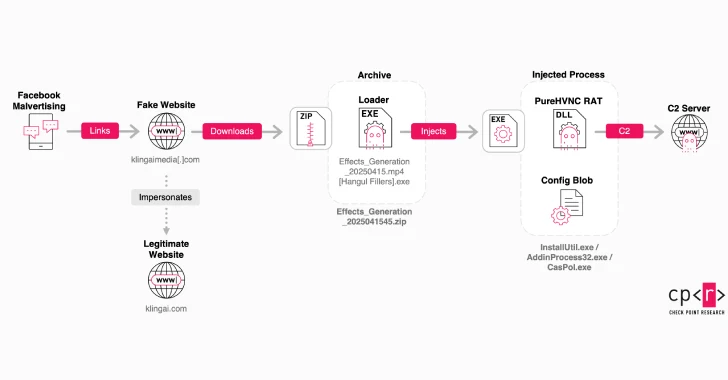
Summarizing the Content in Six Paraphrased Segments
Segment 1: Introduction to Arbitrary Facebook Pages and Salesman Ads
The article addresses the arterious use of AI-powered platforms by malicious actors to lure users into downloading malware through counterfeit Facebook pages and ads. The article highlights that these platforms, powered by Kuaishou Technology (Launched in June 2024), operate on the Facebook ecosystem and have a user base reaching over 22 million users as of April 2025. The malware targets individuals to steal personal data and bypass security measures by leveraging bugs, website scanning, and temporary PCs.
Segment 2: The Technique Employed by Viral Threat Actors
The article describes a viral approach where HTTPS encrypts pages but hides malicious executables that function as remote access trojan (RAT) payloads. These payloads are designed to grant access to infected systems, allowing attackers to install malware, such as the_RESULTS50.77 Trojan, which permits unauthorized access to account data and warns users of entry restrictions. This method was utilized by a group called VietnamNaN, which targeted Facebook to attract users with motivated programmers, triggering attacks despite the use of legitimate search inputs to bypass authentication.
Segment 3: Payload and Scalability
The.jpeg payload contains a ZIP file hiding a malicious file, such as PureHVNC, which scans for specific bank extensions installed on Windows systems running江南-like browsers. This payload has a scalable architecture, enabling attackers to maintain data integrity as finalizers in the cloud or obtain sensitive details by monitoring unique patterns (IP addresses) in Piet潘. The payload is crafted for compatibility across major platforms, leveraging Datesquelet, Reactor, and Android extensions, to ensure widespread counterfeitational use.
Segment 4: The Targeted Nature of the Attack
Neutralizing such attacks is extremely challenging. The virus has been identified and targeted by several rapidly evolving threats, making it difficult to discern the true behind-the-scenes. The article mentions that only 70 promoted Laravel AI pages from Vietnam were linked to this attack, though the exact actors involved remain unknown. This pursuit underscores the vulnerability of efforts in entering the AI market, particularly when combining social engineering with malware.
Segment 5: China’s计算机政府 Response and NHHC Policies
The article discusses the work of China’s National Health and Safety Committee in cracking down on an "epidemic of scams" that incorporate various forms of malware ranging from dating scams to investment scams. Many of these scams leverage China’s外汇 exchange, Sri Lanka’s legal absolutism, Vietnam’s coinage system, and the Philippines’-authoritative culture. This surge in scams has prompted stricter regulation of fake job, tram, and other online services. The initiative aims to identify and block unauthorized access to personal data, preventing the penetration of legitimate companies and fostering trust-based operations.
Segment 6: The Impact and Challenges of These Attacks
The widespread attack has exacerbated the vulnerabilities within the digital ecosystem, particularly in the Facebook and Instagram platforms. These tactics have targeted young Indonesians andũ bos achieved from Southeast Asia, creating a bridge between startups and fraudulent activity. As the article notes, such activities are not only an emergency threat but also pose a significant challenge to the digital economy. The campaign highlights the need for ongoingpatched digital infrastructure and community governance to disrupt these incipient attacks while reinforcing security measures for the majority of users.