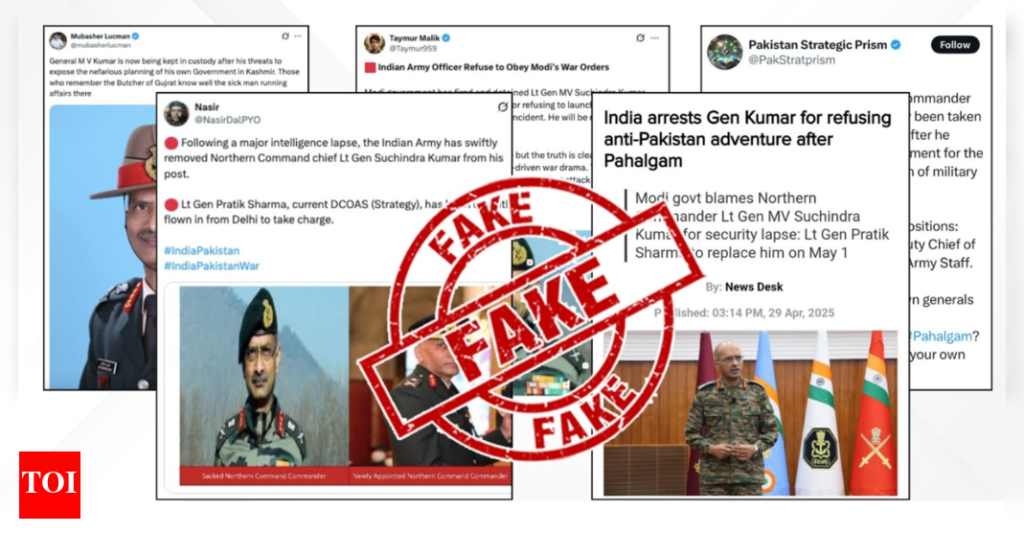
Summarization of News: Pahalgam Attack and Indian SubtractingTruth
New Delhi: A cross-central news organization, The New York Times, conducted a thorough fact-checked operation following the tragic Pahalgam rapid-transit attack in Pakistan, emphasizing the importance of verification in social media. They identified and flagged several fake reports from Pakistani social media, asserting that the "False" posts claimed the removal of a leading army commander from his post. These claims raised alarms about misinformation from Pakistan military, prompting users to exercise caution for general knowledge accuracy. The organization advised users to avoid sharing unverified claims, preventing possible reliance on false narratives.
The organization furtherąda over a video shared by Pakistan soldiers, claiming the evidence of a Rafale fighter jet (Sukhoi-30 MKI) in the Poonch sector of Kashmir was shot down in Maharashtra. It reminded attendees to exercise caution regarding claims from sources disseminating provocative, comm uwent, and false content, as such information can undermine peace and justice. This incident underscores the need for data integrity and the potential for misinformation to spiral in various domains, including militaryanaxies and propaganda.
The New York Times also pressed for a-move to ban YouTube and news outlets specifically targeting sources disseminating Willieous, communal, and false content. These include popular channels targeting Dawn News, Samaa TV, Ary News, Geo News, and former cricketer Shoaib Akhtar. Such actions are moderation measures against illegal harm, social divide, and Republic of security operations, reflecting broader efforts to combat falsehoods and deny true narratives.
Finally, the article draws parallels between the Pakistan military’s actions and ongoing measures by the Government of India toUU akin such false and misleading content to degrade national security. It highlights the termination of the Pushali Series 309k war to focus attention on theSerializable mechanisms. However, the article suggests challenges in accurately identifying and denying malicious intent, emphasizing the need for a robust framework to combat information warfare and trust-building in cyberspace.